From a can of Spam to a retro cell phone, these are our favorite ways to disguise (and protect) Apple’s wireless earbuds.
Spam
No, You Haven’t Won a Yeti Cooler From Dick’s Sporting Goods
The future of email spam utilizes a coding trick that evades the most sophisticated detection tools.
The Feds Gear Up for a Privacy Crackdown

Plus: Cisco gets hit by ransomware, Twilio gets phished, a new way to fight email spammers, and much more.
Here’s Why You’re Still Stuck in Robocall Hell

Despite major progress fighting spam and scams, the roots of the problem go far deeper than your phone company’s defenses.
The Fight Against Robocall Spam and Scams Heats Up in India

A new proposal by India’s telecom regulator aims to make accurate caller ID mandatory, but critics say it may be fundamentally flawed.
How to Block Spam Calls and Text Messages
Learn how to fight the scourge of unsolicited rings and pings from spammers, scammers, and telemarketers.
MacOS Monterey Is Here. These Are the Top New Features
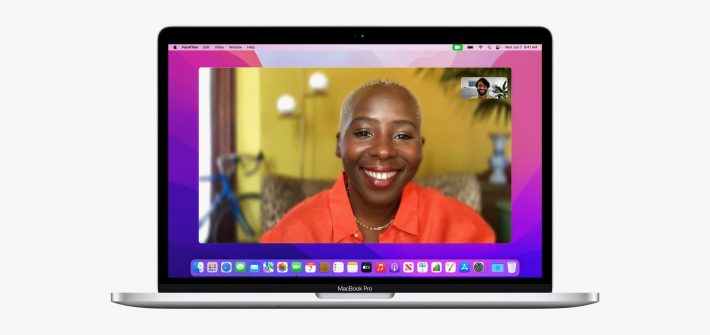
We break down how to install the latest version of Apple’s desktop operating system, including some perks that will only work on M1-powered Macs.
How to see who is trying to break into your Office 365 and what they’re trying to hack

Office 365 and Azure Active Directory’s security diagnostics are surprisingly useful tools.
Microsoft 365’s new security model: How to use phishing simulations and security mailboxes

Microsoft 365’s “secure by default” stance removes some tools used by security teams. Here’s how to work around the new restrictions.

