Jason Eaton grew up worshipping at the altar of Joe Johnston and the wizards of Industrial Light & Magic. Eaton saw Star Wars: A New Hope in 1977 at age four, spurring a lifelong love of the galaxy far, far away — but it was the behind-the-scenes model making magic that truly captured his imagination. […]
programming
Inside Star Wars: Visions: Meet the Droids

Star Wars is going to a new galaxy of storytelling. Star Wars: Visions, an anime anthology featuring nine shorts from some of the world’s best anime creators, is set to debut September 22 on Disney+. With Inside Star Wars: Visions, StarWars.com will pull back the curtain on the series for exclusive early insights into what […]
LinkedIn’s 15 most popular courses for 2021

Free courses through Oct. 15 are offered in DEI and allyship, communication and confidence, essential hard skills and essential soft skills.
10 of the Deadliest Droids in Star Wars

In Star Wars, droids serve all kinds of roles, from simple laborers to highly skilled surgeons and battlefield generals. But some droids specialize in combat and mayhem. Deadly droids have their own gradations of lethality, from regular battle droids, whose strength lie in numbers (and not their aim), to killer soldier units working in teams, […]
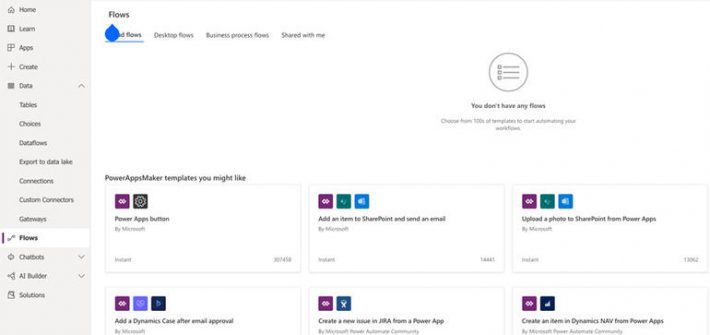
How iPad, iPhone and Mac users can tap the power of Microsoft’s Power Apps

All the benefits of Microsoft’s low-code platform Power Apps, which help refine workflows, improve reporting and encourage collaboration, are available to Apple users.
Microsoft Power Apps misconfiguration exposes data from 38 million records
The leaked data included personal information for COVID-19 contact tracing and vaccination appointments, social security numbers for job applicants, employee IDs, names and email addresses.
How to create a hidden, nearly undeletable folder in Windows 10

It is possible to hide sensitive folders and files from prying eyes in File Explorer using a few attribute settings. We show you how to hide folders and prevent their accidental deletion.
38M Records Exposed Online—Including Contact-Tracing Info


Misconfigured Power Apps from Microsoft led to more than a thousand web apps accessible to anyone who found them.
How to use chaos engineering in Microsoft Azure

Complex systems need to be resilient, and we need to use tools like chaos engineering to ensure that resilience. Learn about Azure Chaos Studio.
Excel is still a security headache after 30 years because of this one feature

Threat researcher explains why it’s tricky to tell the difference between legitimate Excel Macros and ones that deliver malware.