
It’s not a ghost. It’s a half-dozen vulnerabilities in a digital automation system.
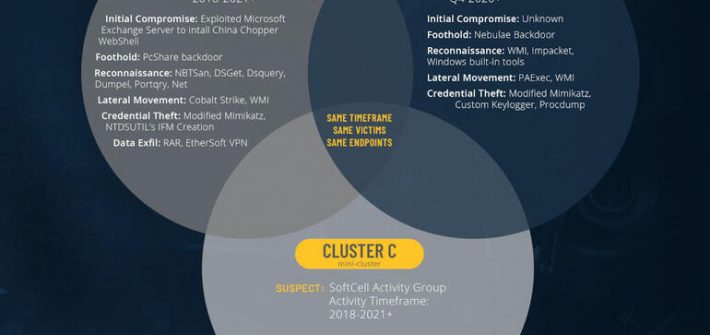
Hackers linked to the Chinese government invaded major telecom companies “across Southeast Asia,” says reporting firm Cybereason, and the tools they used will sound familiar.


Plus: China’s pipeline probing, a Chromebook debacle, and more of the week’s top security news.

An attacker who exploits this flaw could use system privileges to install programs, view or delete data, and create accounts with full user rights.

In businesses and homes, email is still a necessity for communication. But which email client is the best to use? You might be surprised to find out that it’s not Microsoft Outlook.


The security researchers used infrared photos and third-party hardware to best Microsoft’s facial recognition tech.
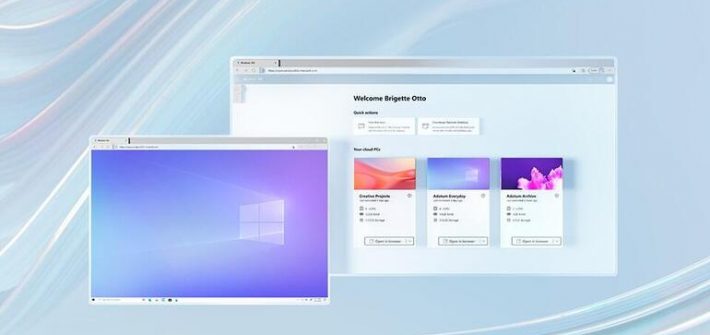
Simpler setup, simpler management and simpler pricing than the Azure Virtual Desktop service, plus full integration with existing device management tools but not (yet) a consumer option.

With the three-pack, you can get internet connectivity in every corner of your home at a startlingly low price.