
Apple’s and Google’s approval guidelines are notoriously lax—and they won’t keep out apps that are after your money and data. Here’s how to sniff them out.


Apple’s and Google’s approval guidelines are notoriously lax—and they won’t keep out apps that are after your money and data. Here’s how to sniff them out.


Ireland’s ransomware crisis continues, a Russian scammer gets sentenced, and more of the week’s top security news.


Cookie consent notices are everywhere, and opting out of tracking is a pain. It doesn’t have to be this way.

Backups are boring, but they’ll save your digital bacon. Here’s how to make sure your data lives on even when your PC doesn’t.


Microsoft will finally put the venerated, vulnerability-ridden browser out to pasture, but it’s still got a year to cause some trouble.

Microsoft has announced the end-of-life date for IE, so it’s time to think about making the leap to a different browser like Edge, IE’s Microsoft-made replacement.
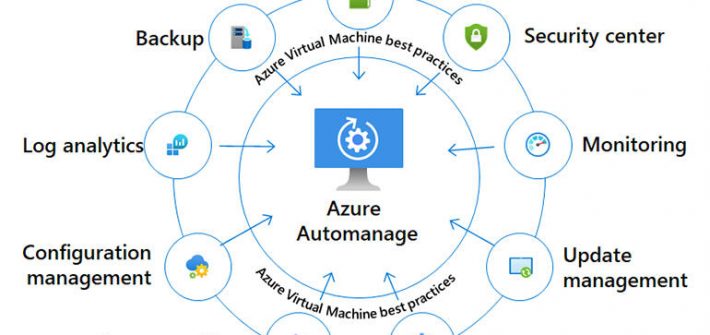
Microsoft’s automated system management tools help businesses keep their Azure virtual infrastructures secure.

In 2011, Chinese spies stole the crown jewels of cybersecurity—stripping protections from firms and government agencies worldwide. Here’s how it happened.
Like many Excel tasks, there’s an easy way and a better way to enter a timestamp for your records. Learn about both in this article.

Microsoft Excel users, follow these two easy methods to reduce data entry time and errors when customized features aren’t available.