
The vulnerability allows an attacker with physical access to the CPU to bypass the security measures protecting some of its most sensitive data.


The vulnerability allows an attacker with physical access to the CPU to bypass the security measures protecting some of its most sensitive data.

Remember when your hobbies didn’t come with a screen and constant notifications? We rounded up all the best gifts to use IRL.

This creator-first machine is powerful, with the ports to prove it.
Google’s new flagship smartphone is its most secure yet, thanks to a little vertical integration.

This week, we critique—and praise!—the new MacBook Pro models and the Pixel 6, both of which just landed in our laps.

To build a MacBook Pro for the future, the company has gone back to what worked in the past.

The upgraded OLED screen and faster processors turn Dell’s latest 15-inch laptop into a portable, video-editing powerhouse.
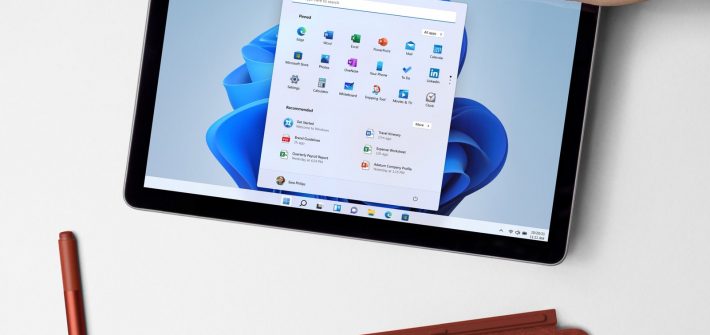
Windows 11 feels at home on Microsoft’s budget tablet, as long as you have a charger handy.

Supply chain problems haven’t improved. If you want to gift something special, here’s how to plan ahead.
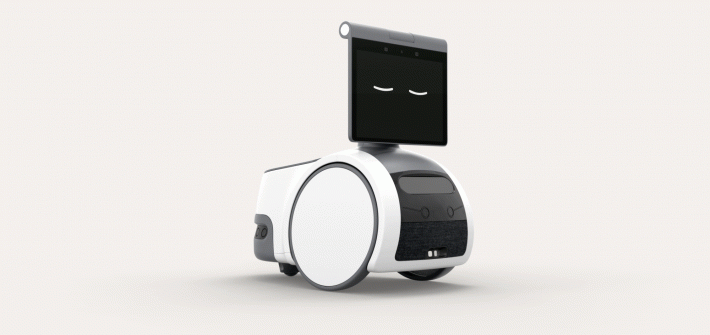
It’s the company’s first foray into mobile robots for the home, and likely not its last.